Internet anonymous IP proxy is a proxy IP technology used on the Internet. It means that using this technology, users can hide their own IP addresses without exposing their real IP addresses, so as to achieve external services without exposing their real IP addresses. IP address. As a new network security technology, Internet anonymous IP proxy can effectively solve the problems of low communication efficiency and poor stability in the current network security business under the client/server (C/S) mode. The emergence of this technology provides a new idea for network security business and a new solution for improving network security business service quality and customer satisfaction.
The working principle of Internet anonymous IP proxy is similar to that of traditional proxy IP technology, but there are obvious differences in terms of usage, specific implementation mechanism, and technological innovation. This article will mainly introduce and analyze the working principle of Internet anonymous IP proxy, its specific application in network security business, and future development trends, hoping to be helpful to relevant practitioners.
operating principle
Anonymous IP proxies are usually composed of servers, proxy IPs and other auxiliary services. When a user accesses the server, the server first converts the user's IP address into its own IP address and forwards it to the user through the anonymous IP proxy; when the user accesses some other auxiliary services, such as domain name resolution, file download, etc., it is forwarded to the user by the anonymous IP proxy Forward the request to these ancillary service providers. The working principle of anonymous IP proxy is very different from the traditional TCP protocol. The traditional TCP protocol is processed based on the data packet itself, while the anonymous IP proxy is processed based on the domain name. Users only need to access a domain name to access any network service. In addition, since anonymous IP proxies can forward requests to different auxiliary service providers, it has great advantages in improving user experience. In a sense, anonymous IP proxy is a "secondary encapsulation" technology, which achieves the effect of "0" being discovered and "1" being hidden by hiding the real IP addresses of the client and server.
Application in network security business
Currently, with the rapid development of information technology, network security business has become an important factor affecting social stability and national security. As the main provider of information security services, network security service providers need to continuously improve their service capabilities to meet customer needs. Anonymous IP proxy technology can effectively solve the problem of traffic cleaning in network security services, thereby further improving network security business service quality and customer satisfaction.
Existing problems and improvement directions
The use of anonymous IP proxies on the Internet has achieved remarkable results, but there are also some problems, mainly including the following aspects:
Data transmission security issues. In the Internet anonymous IP proxy, the interactive information between users and network service providers is realized through the proxy server, and the data transmission security of the proxy server needs to be guaranteed.
In the actual application process of Internet anonymous IP proxy, it will be affected by network congestion, network packet loss and other factors, resulting in obvious delays and packet loss when users use Internet anonymous IP proxy. When applying Internet anonymous IP proxies in network security services, it is necessary to ensure that Internet anonymous IP proxies can maximize the efficiency of network business processing without affecting user experience.
The use of anonymous IP proxies on the Internet is based on the interaction between users and network service providers. How to ensure the security of the data transmission mode between users and network service providers is an important issue. In the actual application process, it is necessary to select the appropriate data transmission mode according to user needs.
Data security protection
In terms of data security protection, through the Internet anonymous IP proxy, users can effectively reduce network traffic and the amount of transmitted data, reduce network communication delays, and improve the stability and reliability of user access based on the user's geographical location or the user's network access method. sex.
At the same time, the Internet anonymous IP proxy can perform real-time data encryption on the content of web pages visited by users, effectively ensuring the security and confidentiality of the website.
For some companies, anonymous IP proxies on the Internet can effectively reduce the security threats faced by websites on the Internet and improve the security and stability of corporate websites.
The application of Internet anonymous IP proxy technology in network security business can effectively reduce the impact of network attacks on customer service and improve customer satisfaction. This makes up for the shortcomings of traditional network security business in terms of user scale and user stickiness to a certain extent. , but as the number of users increases, the advantages brought by this technology will gradually weaken. Therefore, how to further improve the security, reliability and stability of Internet anonymous IP proxy technology, and how to further enhance customer stickiness and enrich customer business scenarios have become key issues in the development of Internet anonymous IP proxy technology.
In the future, the application of Internet anonymous IP proxy technology in network security business will develop in the following aspects: first, continuously enriching the application scenarios of anonymous IP proxy; second, actively exploring methods to anonymize user information and user behavior ; The third is to explore more intelligent and efficient anonymous IP proxy technology. It is believed that as the application scope of Internet anonymous IP proxy technology continues to expand in network security business, it will achieve more significant results.
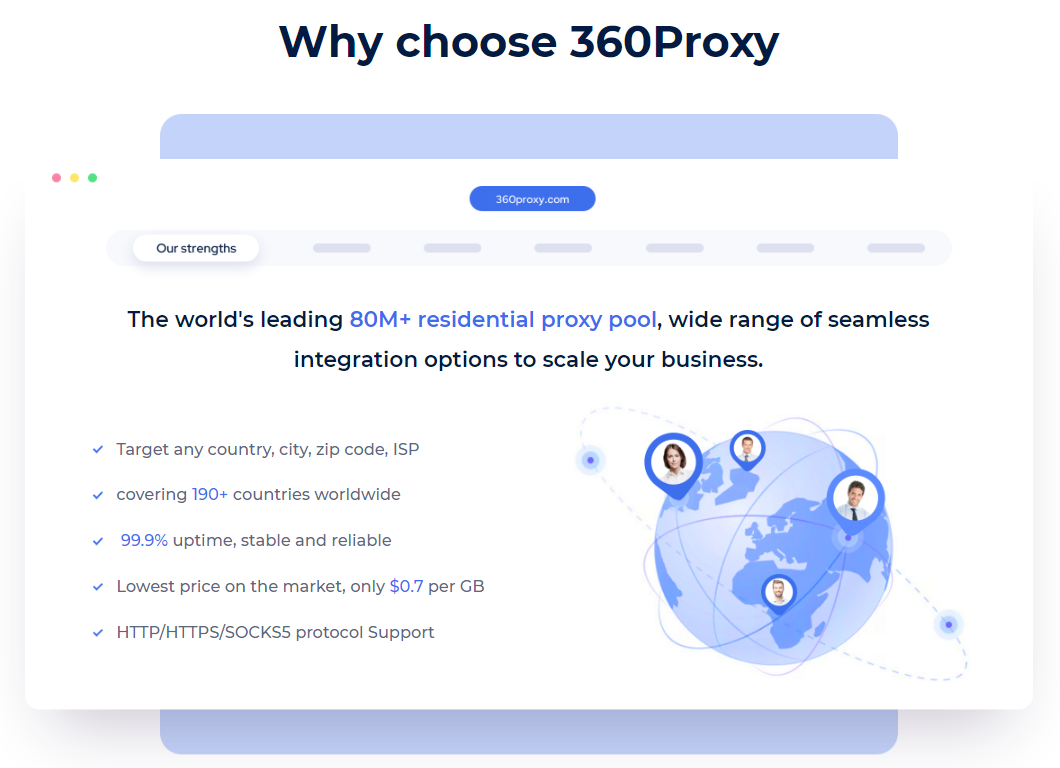
360Proxy provides 100% real residential proxy resources, covering 190+ countries and regions, and 80M+ residential IP resources. To meet the different needs of users, such as media account management, ESTY and SEO optimization, 360Proxy is a good assistant that can provide huge help!
 Username: Password
Username: Password
 Whitelist IP
Whitelist IP
 Proxy Manager
Proxy Manager
 Google Chrome Extension
Google Chrome Extension





























 Dashboard
Dashboard Sign Out
Sign Out






























 USA
USA France
France Brazil
Brazil Vietnam
Vietnam Spain
Spain









