In today's digital world, cybersecurity has become an increasingly important issue. With the rapid development of information technology and the widespread application of the Internet, the risks of cyber attacks and privacy leaks have also increased accordingly. In this context, IP proxy, as an important network tool, not only provides users with a way to hide their identity, but also participates in the construction of network security to a certain extent. This article will delve into the connection between IP proxies and network security, and how to find the balance between concealment and protection.
The basic principles and concealment function of IP proxy
An IP proxy is an intermediary server that hides the user's real IP address by initiating requests on behalf of the user, so that the external server perceives that the source of the request is the IP address of the proxy server. This basic principle provides users with a relatively anonymous way to surf the Internet, effectively meeting the challenges of network tracking and monitoring.
Application of IP proxy in network security
1. Prevent IP tracking
In network attacks, tracking the attacker's IP address is a common method. The use of IP proxy can effectively prevent attackers from being traced to their real IP, improve the attacker's anonymity, and make it more difficult to be punished by law.
2. Break through geographical location restrictions
Certain services or content may be restricted based on a user's geographic location. By using IP proxies, users can disguise their geographical location and access restricted content or services while protecting their privacy.
3. Encrypted communication
Some advanced IP proxy services provide the function of encrypted communication to enhance the security of data transmission. This is crucial for users when transmitting sensitive information on public networks to prevent information from being maliciously intercepted and ensure that privacy is effectively protected.
Finding balance: benign applications of IP proxies
1. Anonymous surfing and legal purposes
The anonymity of IP proxies can be used to protect user privacy, but can also be used for illegal activities. Users should use IP proxies wisely to ensure that their use is legal and does not infringe the rights of others.
2. Security authentication and encrypted communication
Choose security authentication and IP proxy services that provide encrypted communication to ensure that data transmission is protected when using the proxy and reduce the risk of man-in-the-middle attacks and information leakage.
3. Regularly check the security of proxy services
Users should regularly check the security of the IP proxy service they use and pay attention to whether the service provider has taken effective security measures to reduce potential risks.
Intelligent application of IP proxy
1. Intelligent proxy selection algorithm
With the development of technology, the introduction of intelligent proxy selection algorithms allows users to choose the most appropriate proxy service more flexibly. This algorithm can realize intelligent proxy selection and improve the user's online experience based on factors such as user needs, network conditions, and proxy server performance.
2. Innovation of dynamic proxy protocol
Some innovative dynamic proxy protocols are emerging. These protocols further improve the stability and anonymity of proxy services by continuously updating proxy configuration information and adapting to changes in the network environment in real time. Users can consider the application of these new protocols more when choosing proxy services.
IP Proxy Compliance and Regulation
1. Industry standards and specifications
In order to protect the legitimate rights and interests of users, some industry standards and specifications are being formulated to regulate the provision and use of IP proxy services. When selecting services, users can pay attention to and choose IP proxy services that meet relevant standards, thereby improving compliance and regulatory compliance.
2. Government supervision and cooperation
As cyberspace security has received increasing attention, some countries and regions have begun to regulate IP proxy services. Users and proxy service providers should actively respond to the government's regulatory requirements, conduct legal and compliant operations, and maintain the health of the entire network ecosystem.
The future development trend of IP proxy
1. Combination of blockchain technology and IP proxy
The development of blockchain technology provides new possibilities for IP proxies. Through the decentralized characteristics of blockchain, a more secure, transparent, and non-tamperable IP proxy network can be established. This is expected to become an important development trend of IP proxy services in the future.
2. Combination of artificial intelligence and anti-crawler technology
With the continuous upgrading of anti-crawler technology, the intervention of artificial intelligence has enabled IP proxy services to respond more flexibly to various anti-crawler measures. Future IP proxy services may be more intelligent and better adapt to the ever-changing network environment.
Summary and Outlook
The relationship between IP proxy and network security not only involves the balance of concealment and protection, but also includes aspects such as technological innovation, compliance, regulatory compliance, and future development trends. In the process of using IP proxies, users and service providers need to continue to pay attention to the development of technology and improve service levels while also paying attention to compliance and regulatory compliance. With the continuous evolution of technology, IP proxy services are expected to play a more important role in the future, providing users with a safer and more convenient network experience.
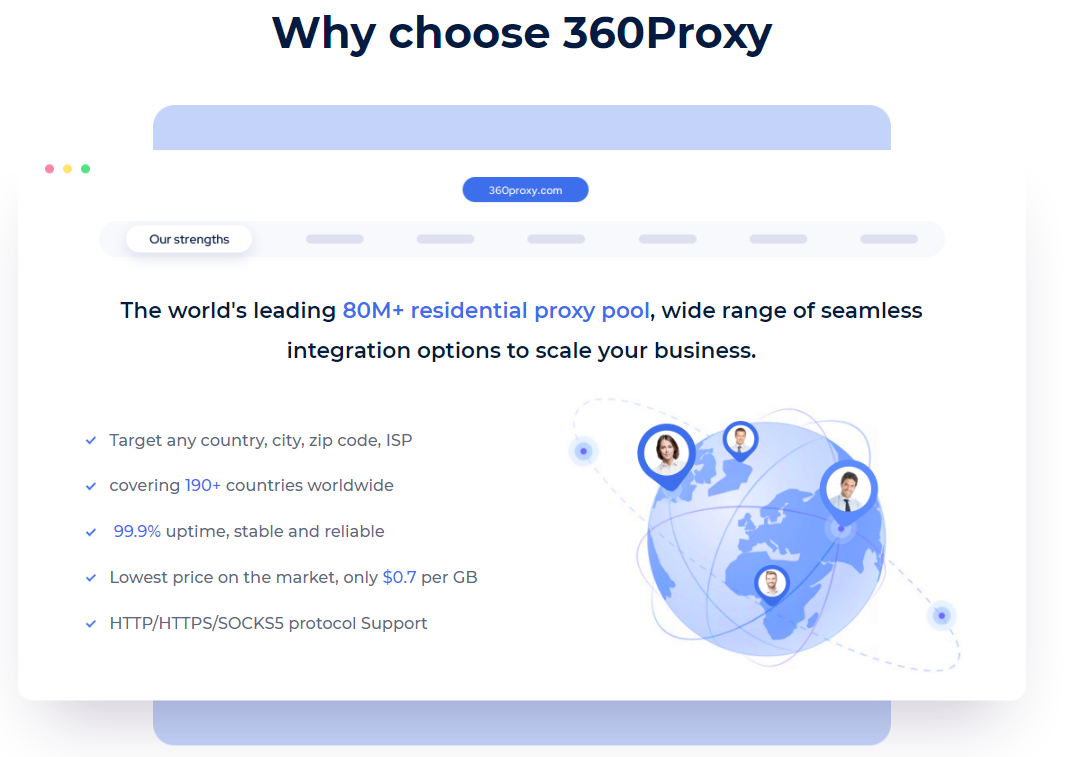
360Proxy provides 100% real residential proxy resources, covering 190+ countries and regions, and 80M+ residential IP resources. To meet the different needs of users, such as media account management, ESTY and SEO optimization, 360Proxy is a good assistant that can provide huge help!
 Username: Password
Username: Password
 Whitelist IP
Whitelist IP
 Proxy Manager
Proxy Manager
 Google Chrome Extension
Google Chrome Extension





























 Dashboard
Dashboard Sign Out
Sign Out






























 USA
USA France
France Brazil
Brazil Vietnam
Vietnam Spain
Spain









