Introduction
With the vigorous development of the Internet, the problem of network security has attracted more and more attention. In this age of information explosion, the protection of personal privacy becomes crucial. As an effective network security tool, anonymous proxy provides an important privacy protection barrier for users by hiding their real IP addresses. This article will delve into the close connection between anonymous proxies and cybersecurity, as well as its role in protecting against cyber attacks and threats.
Basic principles of anonymous proxy:
Before introducing how anonymous proxies can improve network security, it is necessary to understand the fundamentals of anonymous proxies. Anonymous proxy hides the real IP address of the user by forwarding requests and responses in the middle layer between the user and the target server. The existence of this intermediate layer effectively prevents hackers and criminals from directly attacking users, and provides a certain guarantee for network security.
Anonymous proxy and network attack prevention:
An important role of anonymous proxy in network security is to guard against various types of network attacks. By hiding the real IP address of the user, the anonymous proxy effectively avoids the possibility of direct attackers obtaining the user's location and identity. This has significant implications for preventing cyber threats such as intrusions and denial of service attacks (DDoS).
The dual benefits of anonymous proxy and privacy protection:
Anonymous proxies are not only a network security tool, but also a powerful tool for privacy protection. On the Internet, personal privacy is constantly threatened by tracking and surveillance. By masking the real identity of the user, the anonymous proxy protects the user's behavior on the network from being easily traced, thus enhancing the user's sense of privacy.
Anonymous proxy usage scenarios:
Anonymous proxies are widely used in scenarios that require higher privacy protection, such as anonymous browsing, rights protection activities, and news reporting. In these scenarios, users need to ensure that their identities are not easily exposed, and the use of anonymous proxies becomes an indispensable part of maintaining personal security.
Note on anonymous proxy selection:
Despite the many advantages offered by anonymous proxies, users still need to be careful when choosing an anonymous proxy service. Users need to consider factors such as the reputation, log policy, and speed of the proxy service provider to ensure that the selected anonymous proxy service can truly provide effective privacy protection and network security.
Technical evolution of anonymous proxy:
As technology continues to evolve, so do the forms of anonymous proxies. New encryption technologies, protocol support and intelligent privacy management strategies are emerging to provide users with more secure and reliable anonymous proxy services. Users can also pay attention to these innovative technologies for more advanced privacy protection when choosing an anonymous proxy.
Application of anonymous proxy in enterprise security:
In addition to individual users, businesses can also enhance their network security by using anonymous proxies. In the enterprise security strategy, anonymous proxy can be used to hide the real IP of the enterprise's internal servers and improve the resistance to external threats. At the same time, the use of anonymous proxies can also reduce the risk of information leakage when internal employees perform some sensitive operations.
Anonymous proxies contribute to global Internet freedom:
With the development of the global Internet, some countries have strictly regulated the Internet, limiting freedom of expression and access to information. Anonymous proxies provide users with the means to break through these restrictions and promote a free and open Internet around the world. In some areas where speech is restricted, anonymous proxies have become a powerful tool for users to maintain freedom of information.
Conclusion:
As an important tool in the field of network security, anonymous proxy plays a key role in hiding user identity and preventing network attacks. It provides users with an important security barrier and enables users to conduct various activities on the Internet with more confidence. However, when using an anonymous proxy, users need to be cautious and choose a trusted service provider to ensure the dual protection of network security and privacy. The emerging anonymous proxy technology also provides users with more options to meet the growing needs of network security.
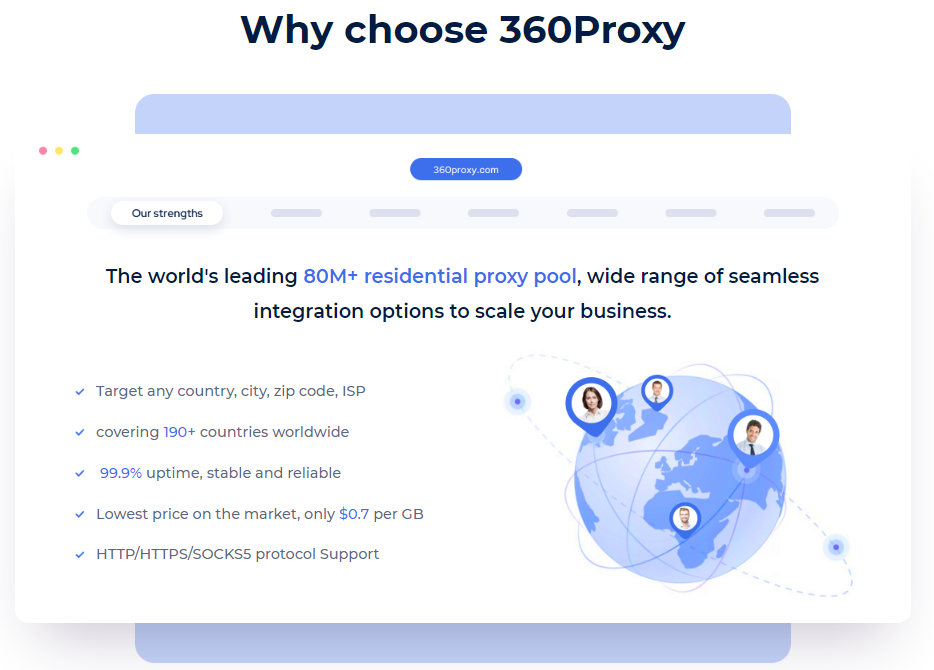
360Proxy provides 100% real residential proxy resources, covering 190+ countries and regions, and 80M+ residential IP resources. To meet the different needs of users, such as media account management, ESTY and SEO, 360Proxy is a good assistant that can provide huge help!
 Username: Password
Username: Password
 Whitelist IP
Whitelist IP
 Proxy Manager
Proxy Manager
 Google Chrome Extension
Google Chrome Extension





























 Dashboard
Dashboard Sign Out
Sign Out






























 USA
USA France
France Brazil
Brazil Vietnam
Vietnam Spain
Spain









