In today's digital age, cyber attacks are becoming increasingly rampant, posing a huge threat to the network security of users and enterprises. As an important part of the network, proxy server can not only improve the network performance, but also play a key role in preventing and mitigating all kinds of network attacks. This article will delve into the relationship between proxy servers and cyber attacks, and how they can work together to build a solid line of defense for cyber security.
Basic functions of proxy servers
The proxy server is the intermediate layer between the user and the target server for forwarding and processing network requests. Its basic functions include:
Caching and acceleration:
Store commonly used data and improve user access speed.
Access control:
Manage and restrict user access to specific resources.
Anonymity and privacy protection:
Hide the real IP address of the user to improve anonymity.
Relationship between proxy servers and network attacks
Proxy servers play a complex and critical role in cyber attacks. It can be used by attackers and can also be used to defend against a variety of network attacks.
1. Proxy server as attack target:
Attackers may attempt to break into and control proxy servers through various means to gain access to sensitive information, launch distributed denial of service (DDoS) attacks, or serve as a springboard for deeper intrusions.
2. Defense function of the proxy server:
Proxy servers have the potential to defend against network attacks. It can intercept malicious traffic, filter harmful content, and identify abnormal behavior, thus effectively mitigating and preventing a variety of network attacks.
Application of proxy server in network attack
1. Mitigating DDoS attacks:
Proxy servers can share the traffic load, relieve the burden on target servers, detect abnormal traffic and filter out attack traffic, and help defend against distributed denial-of-service attacks.
2. Filter malicious traffic:
By setting rules, the proxy server can detect and filter out the traffic containing malicious code or harmful files, effectively preventing the spread of network viruses and malicious software.
3. Anonymity protection:
The proxy server hides the real IP address from the user when they access it, making it difficult for attackers to trace the user's location. This helps protect the anonymity of users on the Internet and reduces the risk of leakage of personal information.
Security measures for proxy servers
1. Strengthen certification and authorization:
By strengthening the authentication and access control mechanisms of proxy servers, you can effectively reduce unauthorized access and improve security.
2. Encrypted communication:
An encryption protocol (such as SSL/TLS) is used to protect the communication between the proxy server and the user, preventing data from being eavesdropped and tampered with during transmission.
3. Regular update and monitoring:
Update proxy server software periodically and apply security patches in a timely manner. By monitoring the running status of proxy servers in real time, you can discover and respond to potential security threats in a timely manner.
Future development direction
As network threats continue to evolve, proxy servers will continue to develop their security capabilities. Future directions may include:
Intelligent Analytics:
Use artificial intelligence and machine learning technology to analyze network traffic in real time and improve the ability to detect and prevent network attacks.
Blockchain technology application:
Use blockchain to establish a decentralized proxy server network to enhance attack resistance and anonymity.
Conclusion
Proxy server plays a key role in preventing network attacks. With their capabilities to mitigate DDoS attacks, filter malicious traffic, and provide anonymity, proxy servers become an integral part of building a solid line of defense for network security. However, to ensure its effectiveness, users and businesses should take appropriate security measures and keep a close eye on proxy server software updates and upgrades to adapt to changing cyber threats.
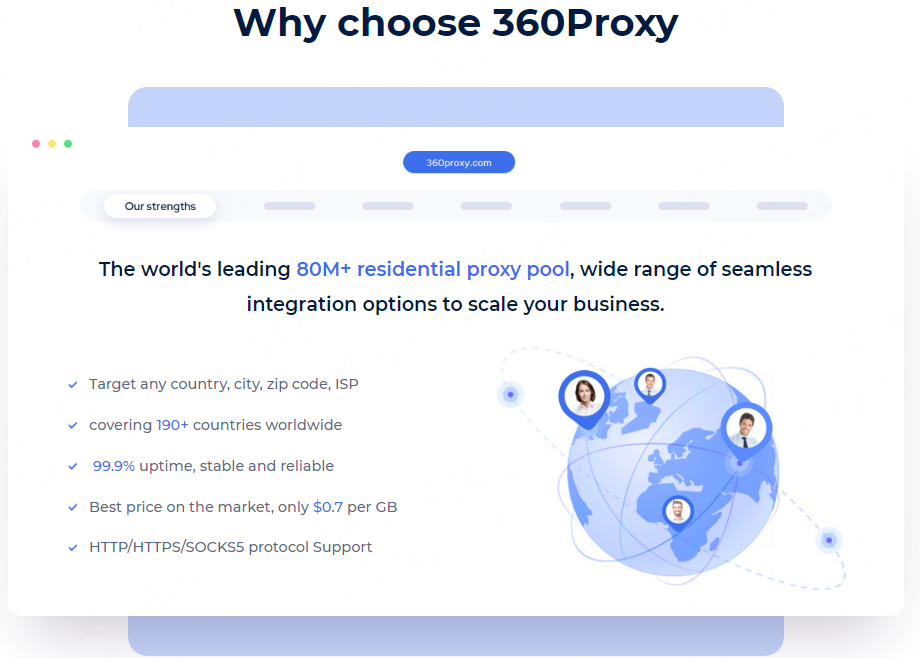
360Proxy provides 100% real residential proxy resources, covering 190+ countries and regions, and 80M+ residential IP resources. To meet the different needs of users, such as media account management, ESTY and SEO, 360Proxy is a good assistant that can provide huge help!
 Username: Password
Username: Password
 Whitelist IP
Whitelist IP
 Proxy Manager
Proxy Manager
 Google Chrome Extension
Google Chrome Extension





























 Dashboard
Dashboard Sign Out
Sign Out






























 USA
USA France
France Brazil
Brazil Vietnam
Vietnam Spain
Spain









